PicoCTF - "hideme"
Solving "hideme" by Geoffrey Njogu
See the challenge by Geoffrey Njogu
Description
The SOC analyst saw one image been sent back and forth between two people. They decided to investigate and found out that there was more than what meets the eye here.
Solution
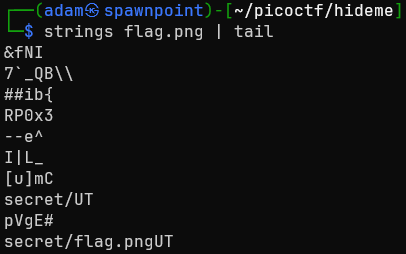
We’re given one file, flag.png. The problem did have a steganography tag, so it was fairly obvious where to start. strings spat out some possibly useful info? As you can see:
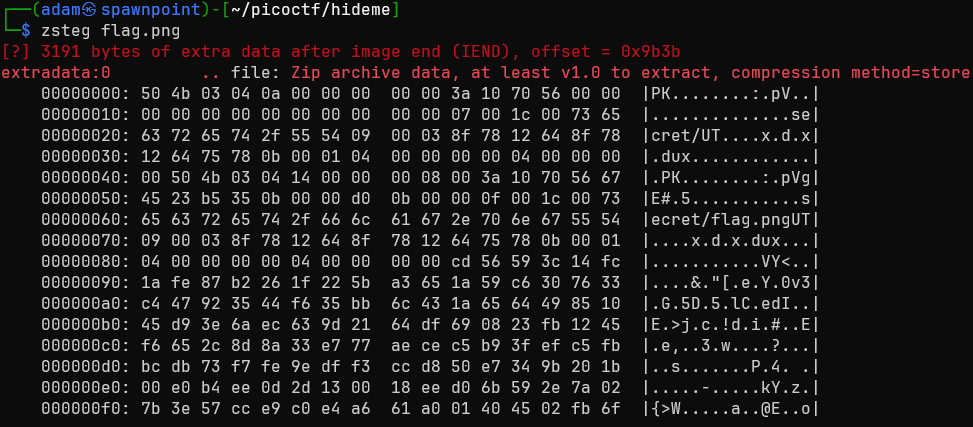
Ok, I’ll check with zsteg then.
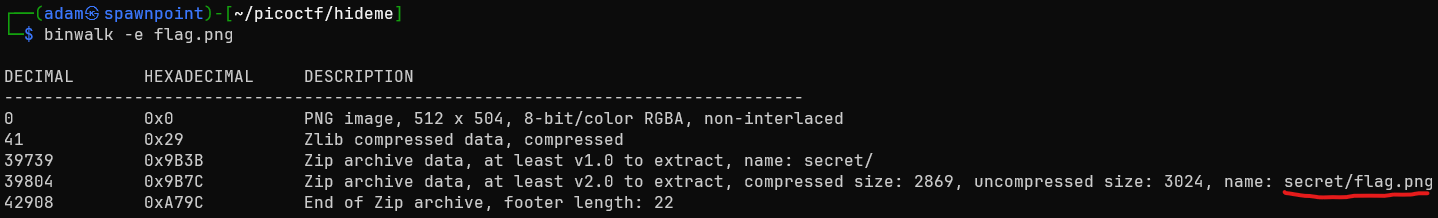
Ah, some data after the end of the image. A zip archive! Okay. I used binwalk to extract it.
Progress! The extracted data contained a secret folder, which contained another flag.png. But this time, it was actually the flag!
This was easy enough to extract with OCR (thanks, windows snipping tool) and then hand correct.
That was a fun one!