PicoCTF - "FindAndOpen"
Solving "FindAndOpen" by Mubarak Mikail
See the challenge by Mubarak Mikail
Description
Someone might have hidden the password in the trace file. Find the key to unlock this file. This tracefile might be good to analyze.
Solution
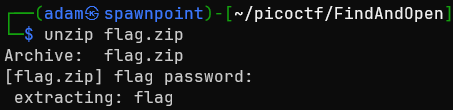
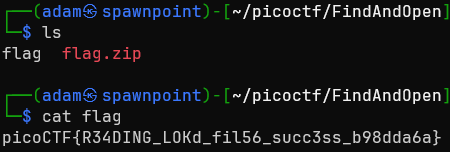
We get two files: dump.pcap and flag.zip. Trying to unzip the flag…
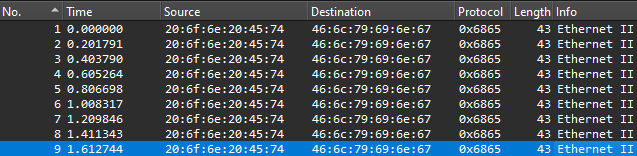
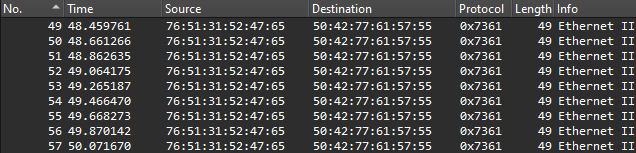
it’s password protected! Ok, I guess we need to find the password somewhere in the pcap file then. Opening it up in wireshark, there’s several distinct groups of packets, some of which have unknown protocols. I figure those are the one’s I should focus on. Of the first section, there are nine packets, all of which are identical.
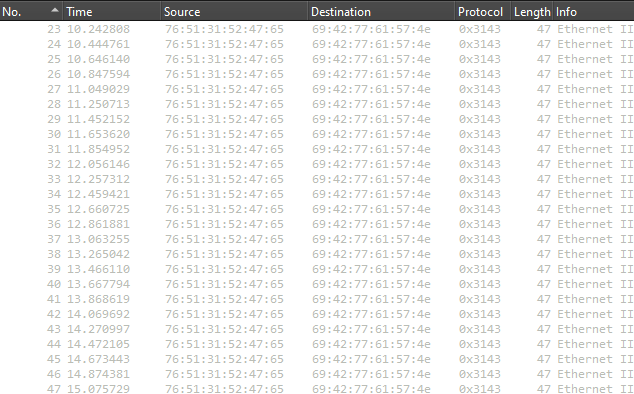
Next, there’s a group of MDNS packets. These don’t appear to contain anything useful or out of the ordinary. Then, some more packets with an unkown protocol.
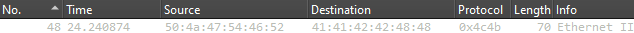
Followed by a single packet with a different, but still unknown, protocol.
Yet more unknown packets.
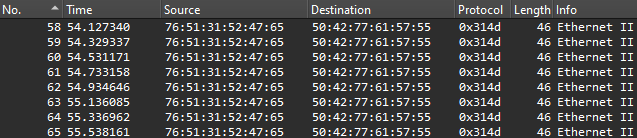
Finally, there’s another group of MDNS packets, which again, look normal. Across the non-MDNS packets, these strings are found (with corrected spelling):
1
2
3
4
5
1. Ethernet secret: Is this the flag
2. Could the flag have been splitted?
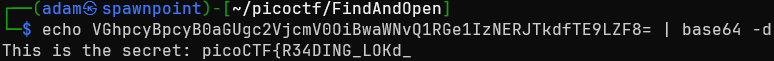
3. VGhpcyBpcyB0aGUgc2VjcmV0OiBwaWNvQ1RGe1IzNERJTkdfTE9LZF8=
4. bababkjaASKBKSBACVVAVSDDSSSSDSKJBJS
5. Maybe try checking the other file
String #3 there looks suspiciously like it’s Base64 encoded, no?
Got it! That’s clearly part of the flag, but not all of it. The leading text makes me think it’s the password…
Bingo!
That felt like it involved a lot more steps than previous challenges, but it helped me get a bit more familiar with wireshark and I had a lot of fun with this challenge!